Resource Center
BayView Medical Clinic
Maintenance was not, and could not be done at all until GFI LanGuard was installed - Dr. Rob Carruthers
Compania De Seguros La Chilena Consolidada
GFI LanGuard does what it is supposed to do in a simple and efficient manner - Oscar Wilton
FrugalBrothers Software
It keeps your networks secure -- which keeps the bad guys out - Bruce Naylor
National Theatre
GFI LanGuard proved to be the solution that the National Theatre was looking for in terms of cost, efficiency and effectiveness - Richard Bevan
Product Releases
Check out the latest product development, including product launches, releases, and upgrades for GFI LanGuard
System Requirements
Check out the system requirements, specifications and other important details about GFI LanGuard
5 security mistakes SMBs make and their simple solutions
What are the top five security errors that small and medium-size businesses (SMBs) commonly make? And how can you avoid them? Watch this video for some simple but solid advice and practical tips to increase your organization's network security.
Choosing the right patch management software
A recent Ponemon Institute study estimates it costs businesses $214 per single, compromised record - so just imagine what it would cost if thousands of records on your system were compromised. Add to that the impact on reputation, lost business and potential legal ramifications and it is easy to see the additional value provided by automatic vulnerability scanning.
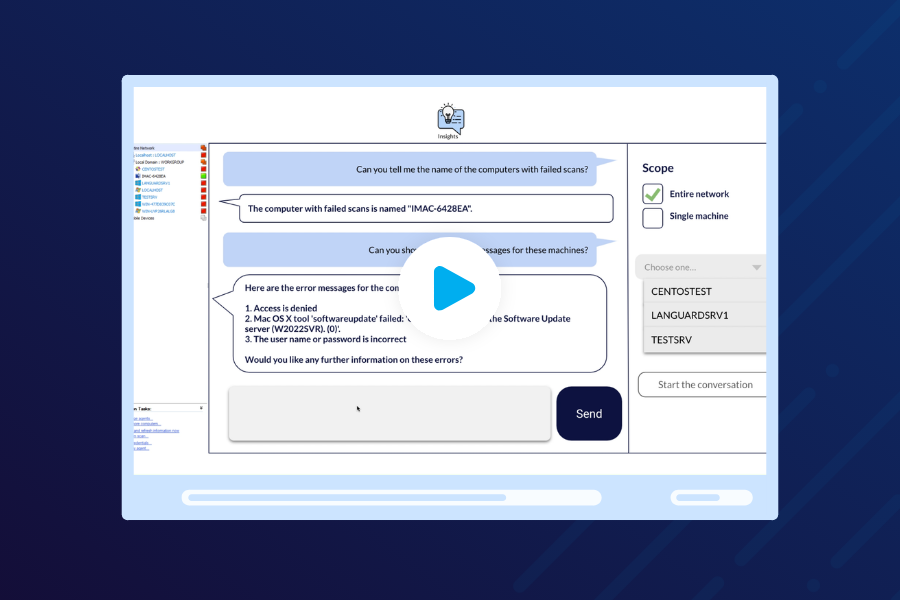
CoPilot in Action
Discover the next level of network security with GFI LanGuard, now amplified by GenAI insights and Configuration Assistant. Watch this demo video to see how it works.

Customer Testimonial, Bayview Medical Clinic
All Paper documents are scanned as searchable PDFs and then attached to the patient chart. Since so much personal data is stored digitally the clinic decided to up their security game and started using GFI LanGuard.
Customer Testimonial, FrugalBrothers Software
Since 2006, FrugalBrothers has built its business around providing only the best email protection and network security tools to its customers. FrugalBrothers are certified in all products and is a top GFI Gold Level Partner.

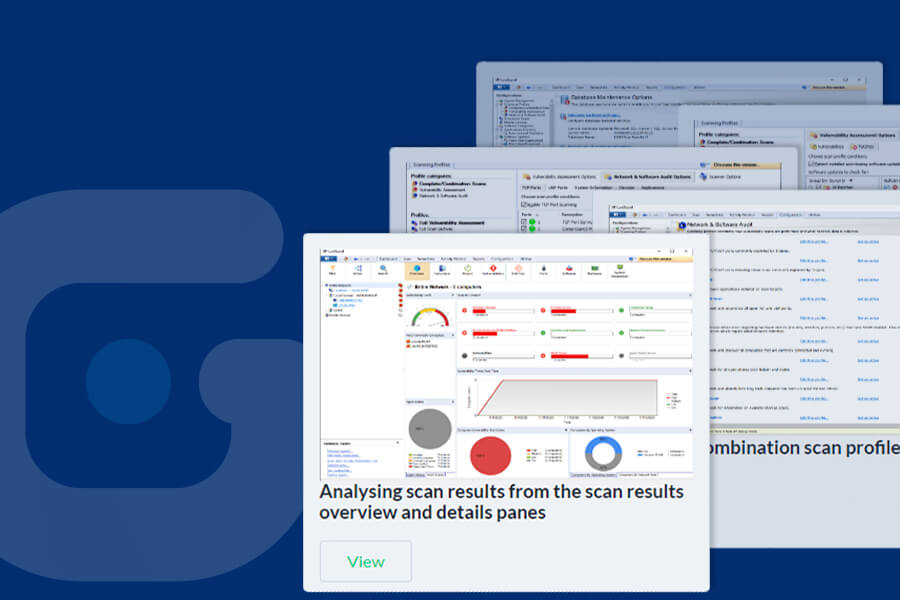
GFI LanGuard Step by step guide
GFI LanGuard is a leading network security scanner and patch management solution that acts as a virtual security consultant. It gives you a complete picture of your network setup, provides risk analysis and helps you maintain a secure and compliant network with minimal effort. So how does LanGuard work?

How to acknowledge or adjust the severity for security vulnerabilities with GFI LanGuard
This short video shows a GFI LanGuard user how to acknowledge a vulnerability so that it will continue to be reported, or ignore it either indefinitely or for a limited time frame.
How to audit smartphones and tablets with GFI LanGuard
This short video shows how to audit smartphones and tablets with GFI LanGuard.
How to automate deployment of patches with GFI LanGuard
This short video shows how to use GFI LanGuard to automatically deploy patches to devices in the network, that have already been tested or manually approved for distribution.
How to automatically discover new devices on your network with GFI LanGuard
This short "How To" video shows how a user can set up an automatic report that will alert them when a new device is added to a domain or organizational unit in the network.
How to deploy Adobe Reader with GFI LanGuard
Watch this video to learn how to deploy Adobe Reader by using GFI LanGuard’s application deployment capabilities.

How to deploy agents with GFI LanGuard
This short video shows a user how to deploy scanning agents to known devices in the network, and to automatically install agents on new devices that connect to the network.

How to deploy custom software with GFI LanGuard
This short video shows a user how to deploy custom software using GFI LanGuard.

How to deploy missing patches with GFI LanGuard
This short video shows how a user can deploy missing patches with GFI LanGuard.
How to find what is shared on your network and is accessible to everyone with GFI LanGuard
This video shows how a user can find what is shared on a network as well as what is accessible to everyone with GFI LanGuard.
How to find what machines have a specific application installed with GFI LanGuard
GFI LanGuard ships with a number of predefined software categories that can help to easily locate and group applications by functional category, e.g. antivirus or firewalls. This short video shows a user how to do this.
How to find what machines have a specific port open with GFI LanGuard
This short video shows a user how to do easily audit open ports on machines in their network and discover such information.
How to perform a remote agentless scan with GFI LanGuard
The short video shows users to perform a remote agentless scan.

How to perform remote network security audits with GFI LanGuard
This short video shows a user how to select a scan target - it can be a local computer, a remote computer, a domain or a workgroup, an Active Directory, organizational unit or an IP address range - create a scan profile and execute or schedule the scan using GFI LanGuard.
How to send email notifications to mobile device owners with GFI LanGuard
Using GFI LanGuard IT administrators can then notify device owners of the latest updates available for the operating systems installed on their devices, and can provide an email template to help IT administrators do this. This short video shows users how this can been done.
How to send reports to email recipients on a regular schedule with GFI LanGuard
This short video shows a user how to configure GFI LanGuard to generate reports which can be scheduled to be run on a regular basis, and to be automatically saved on the disk in a specified location or sent to an chosen email recipient.
How to uninstall unauthorized applications with GFI LanGuard
GFI LanGuard not only provides visibility as to what applications are installed on network devices, but it also provides the capability to uninstall and remove unauthorized applications (such as games, audio/media streaming applications, illegal sharing/P2P applications) from machines and the network. This short video describes how users can do this.
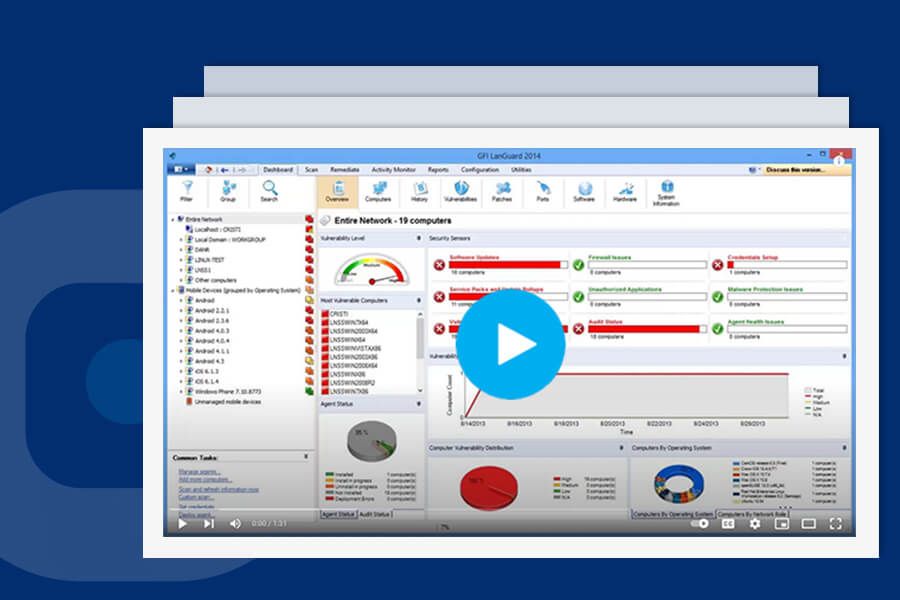
How to use the Dashboard to analyze the scan results with GFI LanGuard
This short video shows a user how to use the dashboard.
How to use the remediate section with GFI LanGuard
This short video shows a GFI LanGuard user how to use the 'Remediate Section' to take actions such as deploying or rolling back updates (both security and non-security ones), deploying custom software, scripts and uninstalling unauthorized applications.
How to use the reporting features of GFI LanGuard
This short video shows you how to use the reporting features to best effect.
How to view relevant security changes from the network with GFI LanGuard
This short video shows a GFI LanGuard user how to remain vigilant and in control at all times, by providing ongoing visibility of any relevant security changes made on your network
I have installed GFI LanGuard, now what?
Watch this video to learn what to do once you've installed GFI LanGuard.
Discover the powerful network security features of GFI LanGuard
Thousands of IT admins worldwide use GFI LanGuard to scan networks for vulnerabilities, automate patching, and achieve compliance.
ISO 27001
Develop an understanding of what ISO 27001 is, what its used for and how GFI can help SMBs be ISO 27001 compliant
Patching and vulnerability management
Develop an understanding of where vulnerabilities can be searched for, how vulnerabilities are identified and fixed, how vulnerabilities are influencing security and how LanGuard can help with patch management, auditing, and security scanning
Security Audit Best Practices
Learn more about why security audits are critical for small and medium businesses and how to use GFI LanGuard in a security audit process.

6-Step Guide to Effective Patch Management
Discover how an optimal patch management system helps to manage security and risk.

6-Step Guide to Effective Patch Management
In this whitepaper, we'll delve into a 6-step guide to effective patch management, offering valuable insights to optimize your cybersecurity.

GFI LanGuard - MSP Licensing Guide
In this document, we will walk you through the licensing details for the GFI LanGuard Network Audit subscription for MSPs, which follows a payper-scan model.
GFI LanGuard AI Copilot - Overview
Maximize the value of your GFI LanGuard AI scanner with CoPilot, a powerful AI assistant designed to illuminate your network's inner workings.

GFI LanGuard Datasheet
Learn how GFI LanGuard can help you through this brief product overview.

GFI LanGuard MSP - How to process orders and activate licenses
Whether you want to order or renew your subscription, this guide will show you how to set up your subscription in the WebShop, select your tariff and activate the license.
GFI LanGuard MSP - Overview
In this guide, we'll explore how GFI LanGuard MSP licensing's pay-per-scan monthly billing model can help you offer comprehensive vulnerability and patch management services

GFI LanGuard MSP - Selling vulnerability and patch management as a service
With GFI LanGuard MSP licensing's pay-per-scan monthly billing model, you can now offer comprehensive vulnerability and patch management services to your clients and take your business to new heights.

GFI LanGuard product review from TechGenix
GFI LanGuard review by Brien M. Posey from TechGenix

GFI Voluntary Product Accessibility Template (VPAT)
The purpose of the Voluntary Product Accessibility Template, or VPAT, is to assist Federal contracting officials and other buyers in making preliminary assessments regarding the availability of commercial "Electronic and Information Technology" products and services with features that support accessibility. GFI remains dedicated to accessibility and will provide additional contact information to facilitate more detailed inquiries.

How to perform a network security audit
Organizations large and small often go to great lengths to keep cybercriminals, ransomware, and other threats at bay. GFI LanGuard is easily one of the best tools to evaluate network security.

How to set up GFI LanGuard server - Best practices
Comprehensive guide on configuring GFI LanGuard server, covering installation, setup, and essential steps to enhance network security and patch management.
How to use GFI LanGuard with a pay-per-scan license
This guide focuses on using GFI LanGuard effectively under the "Pay-Per-Scan" or "MSP License" model.

Network security assessment and patch management in the finance industry
Cybercrime in the financial services industry is large and continuously growing, with regulators stepping up their inspections as consumers fight for more online protection. Companies need to be more prepared.

NIS2 Cybersecurity Directive
On November 28th, 2022: The NIS 2 Directive was adopted by the Council of the European Union, replacing the NIS Directive (Directive 2016/1148/EC) in order to improve cybersecurity risk management.

Offering network security audit with GFI LanGuard MSP
In this guide, we will delve into how GFI LanGuard provides a robust and comprehensive solution for conducting network security audits, empowering businesses to stay secure and compliant.

Strengthening network security with GFI LanGuard and GFI Clearview
This document explores the security perspective of using GFI LanGuard in collaboration with GFI ClearView.

Understanding Essential Eight Compliance and Why It Matters
This comprehensive set of strategies focuses on addressing common attack vectors exploited by malicious actors to gain unauthorized access, exfiltrate data, or disrupt operations.